iQuila CAN DO IT IN A FEW CLICKS AND BETTER
Be one of the first to see the future of real connectivity. Google, Microsoft and Amazon connections, faster, smarter and easier than ever before. Create a Layer2 overlay network in minutes across your corporate network or extending to your virtual network with GCP, Azure, AWS and others.
No need for expensive MPLS and SD-WAN connections with iQuila Virtual Extended Network (VEN)
What is an overlay network?
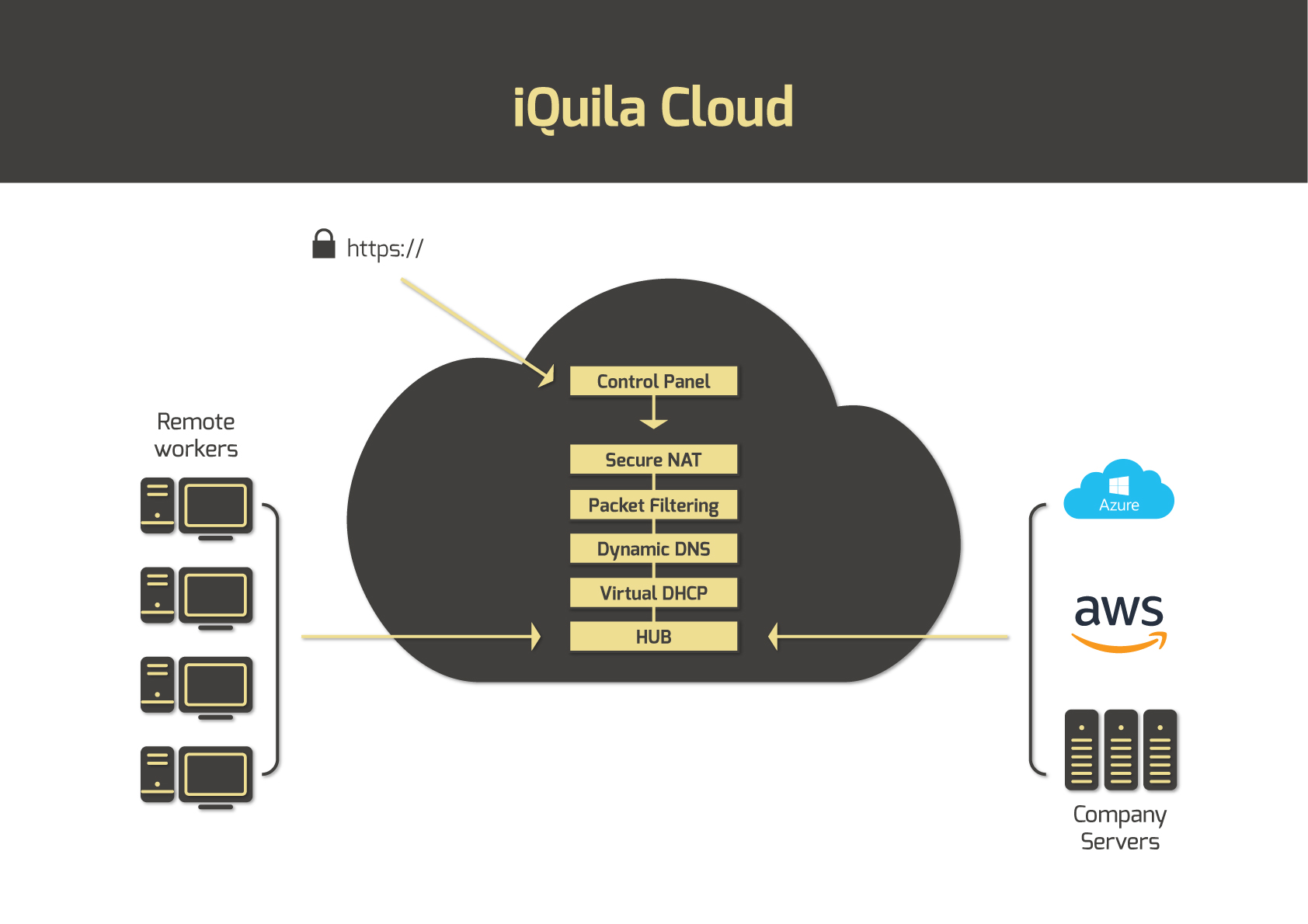
iQuila is a virtual overlay network which runs on top of an existing network. A prime example of this is the internet, which is an overlay network that runs on top of the telecommunications network. Our overlay network is made possible by the iQuila Cloud which creates dedicated client hubs through which all the client’s devices connect. Connection through this hub is made possible by the unique iQuila Client software. This allows all the devices to connect by layer2 across standard internet lines. Devices connected through the iQuila hub become part of your overlay network. If you wish to extend your overlay network to your company network, simply install the iQuila software on all your workstations and remote devices.
iQuila is a cutting edge software based alternative to traditional complex VPN`s which take hours or days to configure. IQuila does not require any expensive hardware and your IT department can build and deploy secure virtual networks in minutes.
Cut time, cut costs and do it better.
iQuila creates a secure software enabled layer 2 connection across the internet or any public or private cloud. The layer 2 connection protocol allows the connection to work with existing network and security structures so the remote device becomes part of the corporate network, iQuila is your LAN port in the cloud.
Remote workers connected to the corporate network subject to active directory security.
iQuila security is a multi-layered approach that protects users and devices wherever they are deployed. With a few clicks you can enforce Active Directory integration, network bandwidth monitoring, deploy security policies and micro segmentation. Network attacks are protected by the key security elements of Encryption - all data is encrypted with 256bit encryption. Virtual network connector - Routes layer 2 connection across WAN with Multi Layer Security - for Device, domain, security certificate and network Secure Connection – We do not need to use static or public I/P addresses.

Have you had any of these problems?
- Connection problems with your VPN?
- ISP’s Blocking your connections?
- Hours spent on the phone to IT Support?
- Trouble accessing the office while abroad?
- Stale cached profiles or locked out?
- VPN takes ages to connect?
- Slow connections making it difficult to work?
To find out more about how we can resolve your IT issues please email or call us:
Send us an email Call us +44 (0)1462 416400













