The SecuraPro™ Framework from Octree
Cyberspace has revolutionised how many of us live and work. The internet, with its more than 3 billion users, is powering economic growth, increasing collaboration and innovation, and creating jobs.
Protecting key information assets is of critical importance to the sustainability and competitiveness of businesses today. Companies need to be on the front foot in terms of their cyber preparedness. Cyber security is all too often thought of as an IT issue, rather than the strategic risk management issue it actually is. And in the UK a small business is hacked successfully every 19 seconds. 39% of businesses suffered cyber-attacks in the past year, with the threat continuing to increase since the onset of COVID in 2020. Small businesses are among those most vulnerable to cyber-attacks. Reasons for this are vast; but include a lack of knowledge, awareness, will to act and even overestimation of their capacity to deal with threats.
Deploying basic technology - such as firewalls and antivirus apps- just won’t cut it, when it comes to protecting your business these days. Staying ahead of cybercrime is tough, but SecuraPro™ makes it simple.
The importance of cyber security awareness
The reality is that our modern reliance on technology has put us in more danger than we could possibly know, as networks become increasingly complex and interconnected. While it isn’t easy or even realistic for every organisation to be able to take full measures against attacks, awareness of threats goes a long way to ensuring that data doesn’t fall into malicious hands or that anything worse happens.
Phishing
Phishing is a type of cyber-attack where the attacker attempts to obtain sensitive information such as usernames, passwords, and credit card details by masquerading as a trustworthy entity when communicating with the victim.
25% of phishing emails get through default Office 365 Security.
Business Email Compromise
Business email compromise (BEC), involves cybercriminals compromising the email account(s) of an employee with access to company finances/funds and using social context to convince employees to send business payments into bank accounts controlled by the criminals. BEC offshoots like billing scams skyrocketed by 155%, in 2020. Meaning any business could be the next to face a huge blow to their data security and financial standing.
Ransomware
Ransomware is malicious software that restricts access to devices infected with it. A significant majority (75%) of IT security professionals predict malware and ransomware to become a larger threat in the future. It encrypts files, demanding payment in exchange for unlocking them and even threatening users to publish or sell the data that’s stolen if they don’t comply.
Hacking
Hacking is the act of circumventing computer security for personal gain. Hacks can be performed by individuals, organised criminal groups or even governments, and are intended to achieve any number of goals, sometimes espionage and sabotage. Usually either exploiting zero-day vulnerabilities, or weak password credentials, many people believe that hackers only go after big-name targets; recent research shows that this definitely isn’t the case.
That’s where we can help
We’ve developed the SecuraPro™ framework to embrace a holistic approach to managing cyber security for today and tomorrow.
Unfortunately, cyber security is all too often thought of as an IT and technology issue, rather than the strategic risk management issue it actually is. With SecuraPro™ we address the three fundamental pillars of cyber security – People, Processes and Technology. Companies are, even now, far too dependent on technology alone to protect critical information assets.
By addressing the vulnerabilities inherent in People, Processes and Technology, SecuraPro™ significantly improves your cyber security profile and reduces the threats you face every hour, of every day.
With three different levels of protection – Essential, Assured and Resilient – the SecuraPro™ framework will help your business foster a culture of knowledge and awareness, where policies and procedures are easily understood and adopted and where technology goes way beyond traditional antivirus software and firewalls.
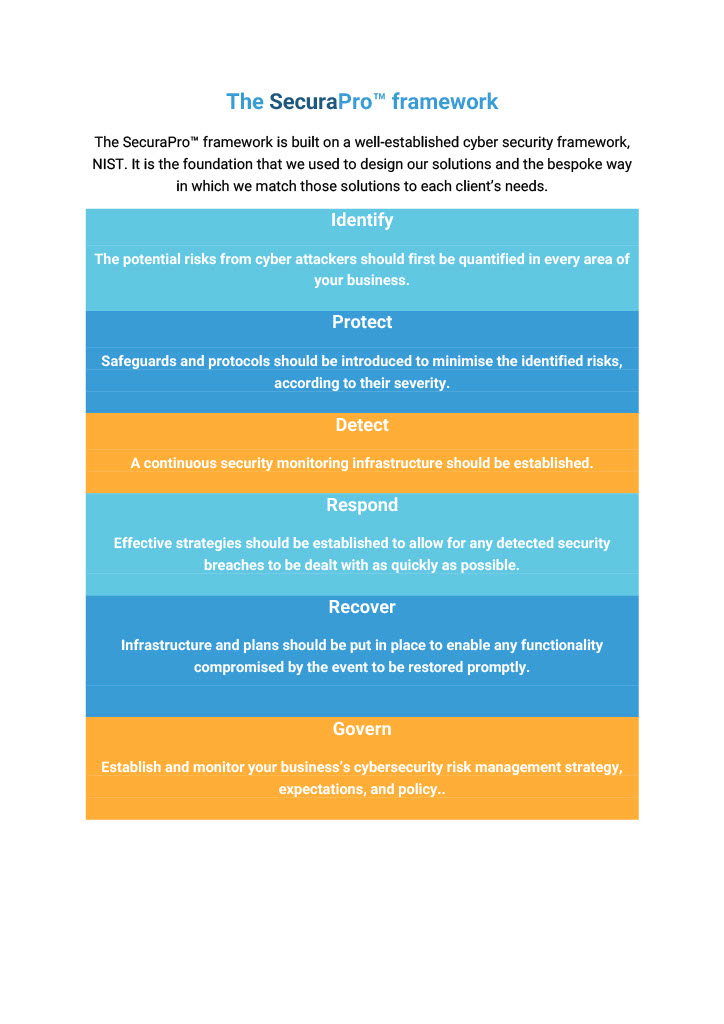
Aligning with the gold standards of cyber security frameworks from NIST (the National Institute for Standards and Technology), ISO (International Organisation for Standardisation) and the UK’s government-backed Cyber Essentials, SecuraPro™ from Octree embraces core cyber security countermeasures specifically aimed at protecting today’s modern digital business.
And you won’t be alone on your cyber security journey. Each of the three SecuraPro™ solutions gives you and your business access to a cyber security consultant to not only ensure your policies are being followed, but to be on hand to answer any questions and provide advice.
Our consultants will be able to guide you through the ever-changing landscape of cyber security enabling you to arm your team with the latest tools to gain an edge against today’s challenges.
A secure silver lining for your business. If you’d like to find out more about Securapro and a structured approach to cost effective security then call us on 01462 416400 or email [email protected].
CYBER SECURITY FOCUSES ON THE FOLLOWING 17 AREAS:
- Governance and Risk Management
- Human Risk Management
- Data Protection and Regulatory Compliance
- Secure Endpoint Configuration
- Mobile Device Management (MDM) and Bring your own Device (BYOD) management
- Identity and Access Management (IAM)
- Business Continuity and Disaster Recovery (BC/DR)
- Vulnerability Management
- Email Security
- Internal Threat Management (ITM)
- Data Loss Prevention (DLP)
- Physical Security
- Data disposal and Destruction
- Employee and 3rd Party Remote Access (Zero Trust Network Access / VPN)
- Cloud Productivity Services
- Secure WiFi Networking
- Web Applications and Content
To find out more about how we can resolve your IT issues please email or call us:
Send us an email Call us +44 (0)1462 416400



















